Using LTS to Quickly Query and Analyze WAF Access Logs
After you authorize WAF to access Log Tank Service (LTS), you can use the WAF logs recorded by LTS for quick and efficient real-time analysis, device O&M management, and analysis of service trends.
This practice uses the access log stream lts-waf-access of log group lts-waf as an example to describe how to use LTS to quickly query and analyze logs.
Prerequisites
- You have connected the website you want to protect to WAF.
- You have enabled LTS for WAF logging.
Procedure
-
Log in to the management console.
-
Click
in the upper left corner of the management console and select a region or project.
-
Click
in the upper left corner of the page and choose Management & Governance -> Log Tank Service.
-
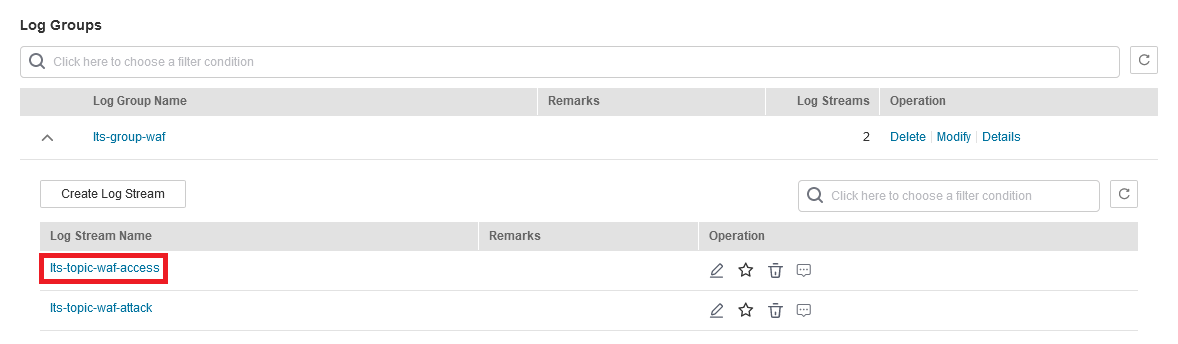
In the Log Group Name column, click the name of the target log group (for example, lts-group-waf) to go the log stream page.
-
In the Log Stream Name column, click the name of the log stream used for WAF access logs (for example, lts-topic-waf-access). Then, select the Log Stream tab.
-
On the log stream details page, click
in the upper right corner. On the page displayed, click the Cloud Structured Parsing tab.
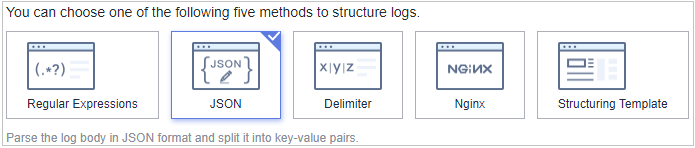
-
Select JSON as the log structure, as shown in figure below:
-
In the Step 1 Select a sample log event. area, click Select from existing log events. In the displayed Select Log Event dialog box, select a log and click OK.
-
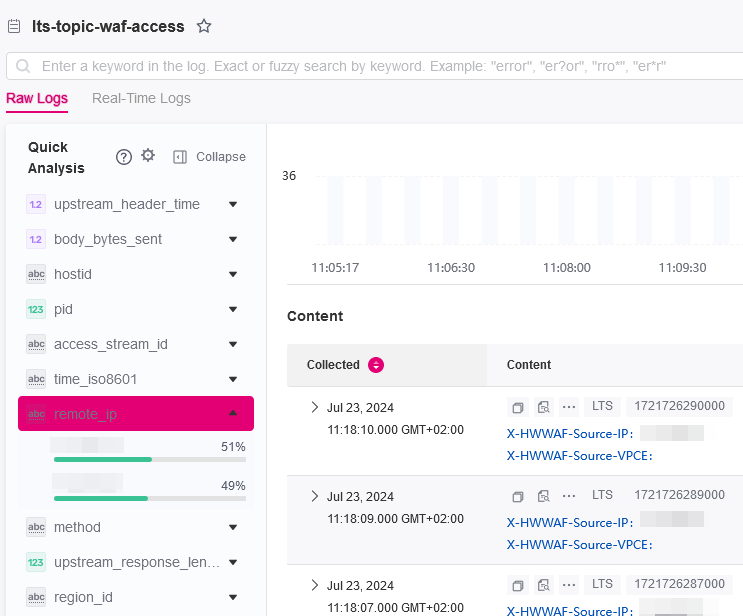
In the Step 2 Extract fields area, click Intelligent Extraction and enable quick analysis for the log field you want to analyze (for example, remote_ip).
remote_ip: IP address of a client from which the request originates.
-
Click Save. Then, LTS will start a quick analysis and do statistics for logs collected in a certain period.
-
In the navigation pane, choose Visualization. On the right pane, select a log query time range, enter an SQL statement in the search box, and click Query to query the specified log.
You can enter either of the following SQL statements in the search box to query logs of a specified IP address:
select * where remote_ip = 'xx.xx.xx.xx'or
select * where remote_ip like 'xx.xx.xx%'